In 2013, WordPress installations around the world were subjected to a global-scale brute force attack.
In 2013, WordPress installations around the world were subjected to a global-scale brute force attack.
These attacks were caused by infected computer networks programmed to attack other vulnerable sites (called “botnets”).
(WordPress is the world’s most used CMS which makes it an obvious target for hacking attacks)
In March 2014, many leading technology sites began reporting that over 162,000 WordPress websites had been hacked.
(160,000+ WordPress sites were attacked in a massive DDoS attack in March 2014. Image: BlogDefender site)
According to the Cnet report,
“With some old-fashioned trickery, hackers were able to get more than 162,000 legitimate WordPress-powered Web sites to mount a distributed-denial-of-service attack against another Web site.”
(Source: cnet.com/news/ddos-attack-is-launched-from-162000-wordpress-sites)
According to leading security firm Sucuri, hackers had leveraged a well-known flaw to attack unsuspecting WP web sites and direct a distributed-denial-of-service cyberattack (DDoS) towards another popular website.
Whenever attacks on WordPress sites take place on such a large scale, it’s natural for people to start questioning if WordPress really is a secure software for running their sites.
Being the world’s most popular CMS makes WordPress an obvious target for hacking. But do you need to be concerned about WordPress as being a secure web platform?
In this article, you will learn some of the main reasons why you should consider using WordPress if you are concerned about website security.
WordPress Security Explained
Let’s start by looking at some facts …
Thousands of websites and blogs are attacked every year … not just WordPress sites!
The sheer number of attacks on websites and blogs worldwide is increasing on a daily basis, and the situation is only going to get worse.
You can safely assume that if your website or blog hasn’t been hacked yet, then it’s inevitable that at some point in time someone will attempt to hack into your site … regardless of the web platform you use!
Since it’s no longer a matter of if, but a matter of when before a malicious user will try to hack your website, are there any advantages that WordPress can offer you in terms of security?
The “Open Source” Software Argument
Many people argue that WordPress cannot be a safe platform for building and running websites and blogs because having open source code means that anyone can view how the software runs.
Open source CMS programs like WordPress, Drupal and Joomla are free to use and anyone has access to the entire underlying code.
The argument against using WordPress, then, goes something like this: If everyone can examine the Open Source code for WordPress, then hackers can easily get hold of all of the code and study every single line, looking for vulnerabilities they could exploit …

(It’s no longer a matter of if, but a matter of when before your website will be targeted by malicious hackers … WordPress or no WordPress!)
While it’s true that WordPress is a free application and hackers can easily go through the code looking for security weaknesses and vulnerabilities they can exploit (hackers can do the same with any software application), the fact that WordPress is a free, open application actually makes it a lot more secure in many ways.
The reason for this is that WordPress has the support of a global community comprised of thousands of software programmers, plugin developers and theme designers who constantly help improve the software and make WordPress more secure …
(With WordPress, a large community of volunteers worldwide is responsible for keeping the core application maintained and updated. Source: WordPress.org)
WordPress evolves because of the effort of a huge volunteer community working around the clock to fix any issues detected by users. It benefits from thousands of web developers, designers and users committed to improving the application and making the WordPress platform safer for every user …
(The WordPress core software is built and maintained by a large community of WordPress users. Image source: make.wordpress.org)
As soon as a security problem is discovered by developers or users, these are then noted in user forums and addressed by the WordPress core development team …
(WordPress is continually being improved by thousands of committed individuals community of web developers and users. Image source: make.wordpress.org)
The WordPress community support system is very responsive and anyone can contribute to the improvement of the software.
For example:
- If you find bugs and a security issue, you can report these by sending an email to security@wordpress.org.
- If you find issues in a WP plugin, you can also report these by emailing plugins@wordpress.org.
This is one of the reasons why the WordPress community is constantly releasing new updates, and why you continually need to keep your site frequently updated …
(WordPress continually releases new version updates to address security weaknesses)
WordPress CMS Vs Proprietary CMS Applications
We’ve just seen that one of the security advantages of using an open source platform like WordPress is that users benefit from a large community of developers who continually contribute to improve code security. By contrast, proprietary or “closed-source” software applications are typically built by a small team of developers with limited time and resources to provide continuous security monitoring, maintenance services, bug fixes and software fixes.
The WordPress CMS is 100% free to download, modify and use, and hundreds of volunteers and expert developers are continually working to improve the technology. Can a proprietary technology company afford to employ as many developers and programmers and still deliver users a completely free CMS software that they can download, use and modify as they wish?
WordPress CMS Vs Other Open Source Platforms

(CMS Platforms)
Whilst on the topic of Open Source content management applications, there is valid research to support the fact that the WordPress CMS is actually safer than other leading Open Source CMS platforms such as Drupal and Joomla.
For example, here is one study showing how many security vulnerabilities were found in each of these open source platforms during a certain period …
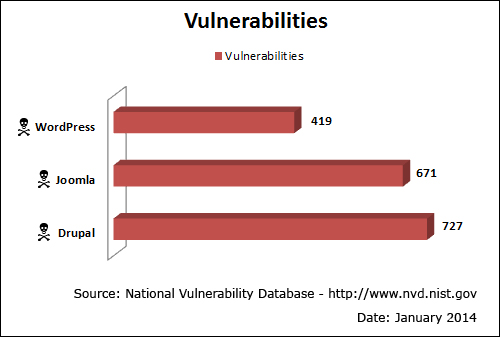
(WordPress has fewer security vulnerabilities than other CMS platforms. Screenshot source: National Vulnerability Database)
Other studies indicate that, because WordPress is easy to use and update, when sites across different CMS platforms were tested for security issues, WordPress sites had a significant degree of less exposure to risk …

(WordPress is more secure than other leading CMS applications. Image source: BlogDefender.com)
Don’t Blame WordPress When Things Go Wrong
When WordPress sites are attacked, don’t be too quick to blame the WordPress CMS platform.
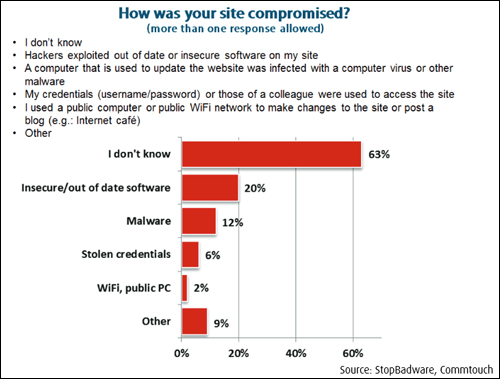
According to a report called “Compromised Websites: An Owner’s Perspective,” which is published by security vendor Commtouch and StopBadware, a nonprofit organization that helps webmasters identify, remediate and prevent website compromises, most website owners are not fully aware of the security threats their websites are exposed to, how to properly secure a website, or how to deal with compromised web security.
In fact, over 60% of webmasters surveyed in this report didn’t even know how their websites had been hacked after an attack …
(Many webmasters don’t even know how their sites get hacked. Image source: StopBadware.org)
Of more immediate concern is the fact that many security issues seem to be related to site owners simply not upgrading their WordPress software to a newer version …
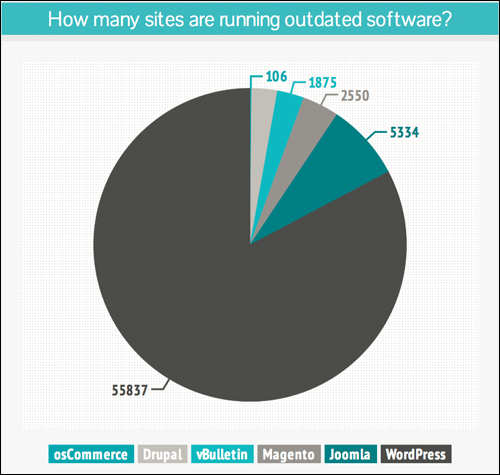
(Many security issues come from sites running an outdated WordPress version. Image source: Sucuri.net)
When WordPress security issues were looked at in more detail, it was found that only between 25% – 30% percent of vulnerabilities discovered in 3rd-party code are actually found in the WordPress core software, while most security issues are found in plug-ins and extensions …
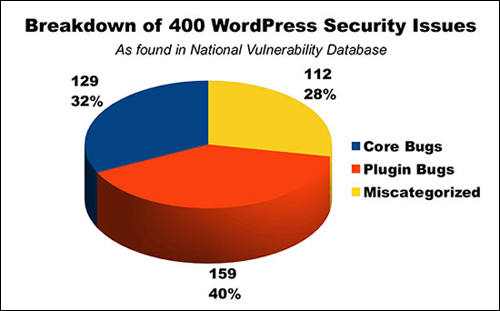
(WordPress Security Issues. Image source: WebDesign.org)
Like many modern web applications, WordPress is regularly updated to address new security threats that can arise. Improving security is an ongoing concern, and to that end, you should always keep your WordPress software, themes, and plugins up-to-date.
WordPress … Good Enough For Banks To Use!
The amount of misinformation about how secure WordPress is has even caused the co-founder of WordPress, Matt Mullenweg, to chime into the online discussion.
In a post entitled “A Bank Website on WordPress” published on April 15, 2015, Matt wrote the following about WordPress security …
There’s a thread on Quora asking “I am powering a bank’s website using WordPress. What security measures should I take?” The answers have mostly been ignorant junk along the lines of “Oh NOES WP is INSECURE! let me take my money out of that bank”, so I wrote one myself, which I’ve copied below.
I agree there’s probably not a ton of benefit to having the online banking / billpay / etc portion of a bank’s website on WordPress, however there is no reason you couldn’t run the front-end and marketing side of the site on WordPress, and in fact you’d be leveraging WordPress’ strength as a content management platform that is flexible, customizable, and easy to update and maintain.
Matt then goes on to provide a couple of security tips, before stating the following …
For an example of a beautiful, responsive banking website built on WordPress, check out Gateway Bank of Mesa AZ. WordPress is also trusted to run sites for some of the largest and most security-conscious organizations in the world, including Facebook, SAP, Glenn Greenwald’s The Intercept, eBay, McAfee, Sophos, GNOME, Mozilla, MIT, Reuters, CNN, Google Ventures, NASA, and literally hundreds more.
As the most widely used CMS in the world, many people use and deploy the open source version of WordPress in a sub-optimal and insecure way, but the same could be said of Linux, Apache, MySQL, Node, Rails, Java, or any widely-used software. It is possible and actually not that hard to run WordPress in a way that is secure enough for a bank, government site, media site, or anything.
Millions of businesses around the world, including banks, leading brands and e-commerce sites choose WordPress to build their websites, not just bloggers.
Other Issues That Can Affect Site Security
Other areas that can affect site security include:
- No platform is completely safe from hacking. As many as 90% of all websites across all platforms are vulnerable to attack, mostly due to software that is out of date.
- The biggest security vulnerability of all CMS platforms seems to be the users themselves. An example of this is users ignoring strong password security practices.
- Lack of constant monitoring. Security processes require frequent monitoring, testing, updating and improvement.
- Server setup. For example, sites on shared webhosting servers are only as secure as the least safe site on the grid, so if another user has a weak FTP password on your shared server, then every site on that shared server is potentially vulnerable to hacking as well.
There Is No Reason Not To Use WordPress
As you can see, WordPress is as secure as most of the leading web platforms being used by businesses of all sizes to build their presence online. As long as you remember to implement basic security measures and keep your WordPress software (and themes, plugins, etc.) regularly updated, there’s no reason why you shouldn’t use WordPress.
![]()
WordPress Security – Useful Tips
To learn about ways to protect your WordPress site from brute-force attacks see this article: Preventing WordPress Brute-Force Attacks
A compromised site provides malicious users with a platform to launch distributed attacks, spread malware and use your website to defraud others. Blog Defender makes your WordPress site invisible to attacks from hackers and bots. Learn more about this plugin here:
If you are currently using an older WordPress version remember to make a complete backup before updating your software to benefit from the latest security updates. This way, if something goes wrong, you can always restore.
If you don’t want to perform manual backups, there are a number of plugins you can use. You can read about a WordPress backup plugin that can fully automate your backup process here: Back Up, Clone And Keep Your WordPress Sites Protected With Backup Creator WP Plugin
![]()
References
For more information on the above, see the following sources:
- ITProPortal.com
- National Vulnerability Database
- BlogDefender.com
- UpAndUpStudios.com
- StopBadware.org
- Sucuri.net
- WebDesign.org
- Quora.com
- Ma.tt
Hopefully, the above post has given you a better understanding of problems that can affect your website and how WordPress can help you improve your business online. To learn more about the security benefits of using WordPress for a business website please see other posts we have published on this site or subscribe to receive updates and notifications when new content is published.
***
"I love the way your email series "Infinite Web Content Creation Training Series" is documented and presented. It is very absorbing and captivating. The links and tutorials are interesting and educational. This has motivated me to rewrite my content following the concepts I am learning from the email series." - Mani Raju, www.fortuneinewaste.com