Being the world’s most popular CMS makes WordPress an easy target for malicious attempts by hackers.
Being the world’s most popular CMS makes WordPress an easy target for malicious attempts by hackers.
In April 2013 a mass brute force attack hit WordPress installations across virtually every web host in existence around the world.
These attacks were caused by botnets (computers infected with malware and programmed to attack other installations with security vulnerabilities).
How To Protect Your WordPress Site From A Brute-Force Attack
Brute Force Attacks – An Overview
A brute-force attack is a technique used to break an encryption or authentication system by trying all possibilities.
(Source: Chinese University Of Hong Kong)
There are many methods hackers use to try and break into a WordPress site. One of these is by trying to guess the site’s administration login username and password. To attempt this, hackers use software tools and scripts that automatically tries to guess hundreds of login possibilities in minutes.
If you’re using obvious user names and weak passwords that are easy to guess, your website can be easily hacked by a malicious script’s repeated attempts to work out your site’s login details.
This is called a “brute force” login attack.
Botnets
A botnet is a number of Internet-connected computers communicating with other similar machines in an effort to complete repetitive tasks and objectives. This can be as mundane as keeping control of an Internet Relay Chat (IRC) channel, or it could be used to send spam email or participate in distributed denial-of-service attacks. The word botnet is a combination of the words robot and network.
(Source: Wikipedia)
”Botnets” are networks of private computers that have been compromised and infected with malicious code or scripts, which are then controlled remotely as a group, often without the unsuspecting computer owners even being aware of this.
Botnets are normally used used to send mass spam emails from the infected computers of compromised user accounts.
The screenshot below was taken from a site that monitors online security showing the locations of the command centers of ZeuS – a botnet that has been actively compromising computer networks all around the world since 2009 …
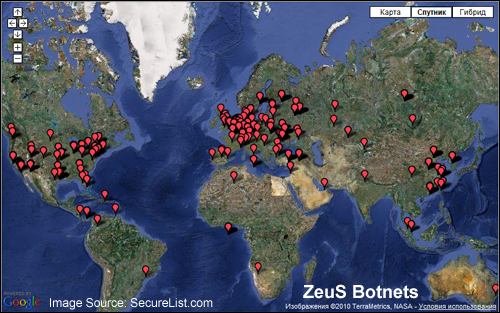
(ZeuS is a botnet that has been actively compromising computer networks all around the globe since 2009. Image source: SecureList.com)
These ongoing botnet attacks are well organized and highly distributed. Over 90,000 IP addresses were identified by a number of webhosting companies just in the initial attack, when the web was flooded with millions of attempts to force their way into WordPress users administration areas. The mass attack then continued, with over 30,000 WordPress sites being hacked each day.
News of the large-scale brute force botnet attack was reported by all the major webhosting companiesand leading technology media publications, such as Forbes, TechNews Daily, Tech Crunch, BBC News, PC Magazine, and even on the official website of the US Department of Homeland Security …
(Being the world’s most popular CMS makes WordPress an obvious target for hacker attacks)
Does This Mean We Should Stop Using WordPress?
No. In fact, there are many great reasons why you should choose WordPress if you are concerned at all about the security of your online business.
We explain why WordPress is a secure platform for websites in this article: Are Open Source Platforms Like WordPress Secure?
![]()
It’s important to note that, in the case of April 2013 brute force botnet attack described above, no specific WordPress vulnerability was being exploited (the same script was also attacking sites built using applications like Joomla).
Mike Little, the co-founder of WordPress, said this about the brute-force attacks:
It is a “simple” script that attempts to login using the admin login and a generated password. So if your password is too short or based on dictionary words it will be guessed and then the script can login legitimately and do whatever it wants including installing scripts (as plugins) or editing files. The attack tries to guess your password, if it succeeds, the most secure site in the world is wide open because they have your password.
Preventing Your WordPress Site From Being Brute Force Attacked – Ten Security Measures
Every site with a vulnerability provides an opportunity to hackers. A vulnerable web site not only offers new hackers opportunities to improve their hacking skills and win “respect” amongst their peers, but it can also serve as a platform for stealth attacks, distributing malware and defrauding visitors through information theft.
If a hacker can break in and gain remote access of your website or blog, the site can then be employed to target more valued web sites.
Additional undesirable impacts of having your website hacked and your site security compromised include getting blacklisted by Google, having stealthy spam links promoting things like online meds, discounted fashion, etc. inserted in your content and page title and descriptions, malicious redirects to phishing sites and other websites, data exfiltration (stealing information or Personal Identifiable Information from your web applications), and many other nasties.
The truth is that hackers are most likely searching for weaknesses and trying to break into your blog at this very moment. Whether they can break in successfully or not, will depend on how hard or easy you will make things for hackers and bots to keep trying until they work out how to get access, or are forced to give up and decide to look for an easier target.
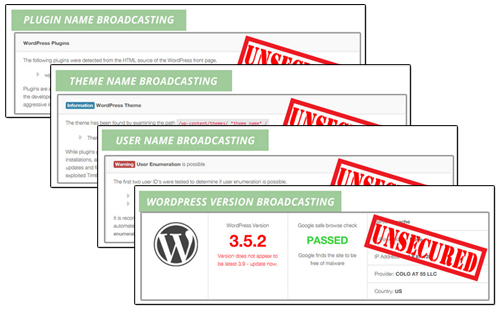
How Much Information Are You Broadcasting To Hackers About Your Site?
Do you own a WordPress site? If so, visit Hackertarget.com and run your website through their WordPress security scan …
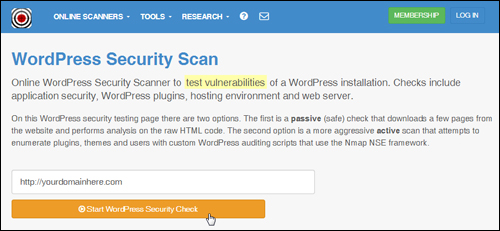 (WordPress Security Check Screenshot image: Hackertarget.com)
(WordPress Security Check Screenshot image: Hackertarget.com)
You will see that the test will yield a number of results and information about your WordPress installation …
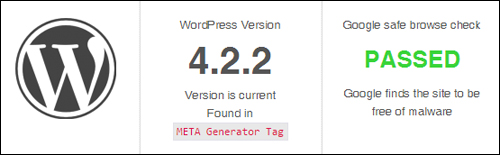
(Hackertarget – website security check results. Screenshot: Hackertarget.com)
It should be obvious after using the tool shown above that if you can freely access all of this information, hackers can too.
The ability to see what version of WordPress you are using, which plugins and themes you have installed, and which files have been uploaded to certain directories on your server can all be valuable information to hackers, as this can inform them about potential security vulnerabilities, especially in older versions.
If your website runs on WordPress and you are not preventive steps to toughen up your site, then it’s practically guaranteed that, at some point in time, your site will be hacked, or at least targeted by bots, because these attacks are systematically targeting WordPress installations all the world!
Typically, when a website gets hacked, webmasters will find themselves completely “locked out” of their own site, or notice that their files have been modified or even that their content has been completely wiped out. Typically, sites will become infected with malicious scripts without the owner’s knowledge or awareness.
To avoid the heartache that comes with discovering that your website or blog has been hacked into, below are 10 essential and effective security measures that will help to protect your WordPress site from brute force attacks.
![]()
Note: A few of the recommended steps below require some technical understanding of how to modify core WordPress and/or server files. If you are not technical, or don’t want to mess around with code on your site, then ask your web host or a professional WordPress technical provider for assistance.
***
Security Measure #1 – Contact Your Hosting Company
Get in touch with your host and ask them what security systems are in place to help prevent your site from brute-force attacks, and what is done to ensure that your WordPress sites get regularly backed up.
Make sure that your webhosting provider regularly backs up your server files and that, if disaster strikes, you can easily get back your site.
Security Measure #2 – Perform Complete WordPress Backups And Keep Your Website Regularly Up-To-Date
You should never rely on your hosting service provider for site backups. Instead, learn how to manage your WordPress site or get this done for you and maintain a habit of religiously performing a complete site maintenance routine frequently (e.g. daily, weekly, fortnightly, etc …)
A proper WordPress maintenance routine ensures that:
- All unnecessary files and data are removed,
- All data and files are free of errors, optimized and backed up,
- All WordPress plugins, themes and software components are up-to-date,
- etc …
A proper WordPress site maintenance routine looks like this …
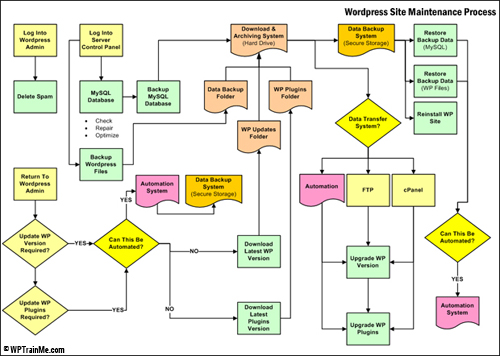 (Maintaining your WordPress website regularly backed up and updated is vitally important for WordPress security. Screenshot image: WPTrainMe.com)
(Maintaining your WordPress website regularly backed up and updated is vitally important for WordPress security. Screenshot image: WPTrainMe.com)
Again, we cannot stress enough how vitally important maintaining your WordPress website completely backed up and up-to-date is. WordPress site maintenance is not hard to do or time-consuming, but it must be done to ensure the security of your website or blog. If you don’t want to learn how to do WordPress site maintenance yourself, pay someone to do it but make sure it gets done. Backing up your website is the next most important thing you must do after making sure that your heart is still beating!
If you don’t want to perform manual backups, there are a number of free and paid plugins you can use. Learn about a WordPress backup plugin that can automate your backup process here: Back Up, Duplicate & Protect Your WP Site With Backup Creator Plugin For WP
Security Measure #3 – Make Sure That Your Username Is Not “Admin”
The large scale brute force botnet attack on WordPress sites was mostly an attempt to compromise site admin panels and gain access to sites by exploiting WP sites with “admin” as their user name.
For website security reasons, never set up a WordPress site with the username admin. This is the first area of potential vulnerability hackers will test. If your site’s user name is “admin”, then change it immediately.
For a detailed step-by-step tutorial created especially for non-technical admin users that shows you how to change your username, go here: How To Change Your WordPress Username From Admin To A More Secure Username
Security Measure #4 – Use A Strong Password
A “brute force” attack occurs when a malicious script continually tries to guess the right password and username character string that will unlock your website.
Unless you put some measure in place to stop the brute force attack from happening (see further below for a couple of simple and effective ways to do this), the “bot” will just continue to attack your site until it eventually “cracks” the code.
Passwords that are easy to guess, therefore, become really easy targets for brute-force attacks. Make sure that you change your password to something that is at least eight or nine characters long, with upper and lowercase letters, and add a few “special” characters (e.g. %, #, @, etc).
![]()
Roboform is a password management tool that lets you easily generate secure passwords …
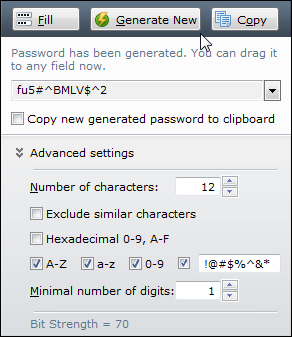 (Roboform is a password management tool that lets you generate different strong login passwords)
(Roboform is a password management tool that lets you generate different strong login passwords)
For a detailed step-by-step tutorial created especially for non-technical WordPress admin users that shows you how to change your password, go here: What To Do If You Need To Reset Passwords
Security Measure #5 – Prevent Access To Your wp-config.php File
The wp-config.php file allows WordPress to communicate with the database to store and retrieve data and is used to define advanced WordPress options.
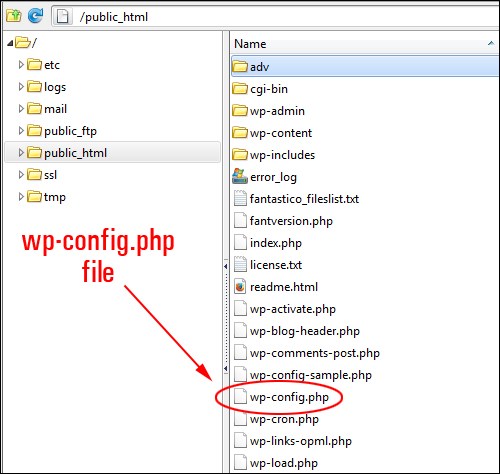
(wp-config.php file)
If hackers break into your site, they will normally search for the wp-config.php file, because this is the file that contains your database information, security keys, etc. Getting access to this information would allow someone to change anything in your database, create a user account, upload files and take control of your site.
To protect your WordPress site from being attacked and even being used as part of a bot net, therefore, you must prevent your wp-config.php file from being accessible. This requires knowing how to edit database information, move files around in your server and changing access permissions.
Security Measure #6 – Rename Or Delete Unnecessary WordPress Installation Files
Rename or delete the install.php, upgrade.php and readme.html files from your server.
These files can be deleted after installation. If you don’t want to delete these files, just rename them.
Security Measure #7 – Upgrade Your WordPress Installation, Plugins & Themes To Their Latest Version
Hackers are always on the lookout for vulnerabilities they can exploit in older versions of WordPress, including outdated versions of WP themes and plugins.
Ensure that all of your WordPress files, themes, plugins, etc. are always up to date.
Security Measure #8 – Disable Your Theme Editor
WordPress comes with a built-in editor feature that lets site administrators edit theme and plugin files from the dashboard area.
You can access the WordPress Theme Editor by selecting Appearance > Editor in your dashboard menu …
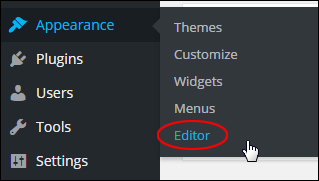
(The WordPress theme editor is accessible using the dashboard menu)
This means that anyone logging into your blog can view and modify your WP theme files, or cause mayhem on your site.
To prevent unauthorized people from being able to access the WordPress Theme editor, you will need to disable it. This can be done by adding code to your wp-config.php file.
Security Measure #9 – Protect Your Site’s Uploads Folder
The WordPress “uploads” folder contains all the media that gets uploaded to your site.
By default, this folder is visible to anyone online. All a person needs to do to view all of the contents in your site’s “uploads” directory is visit your directory using a web browser …
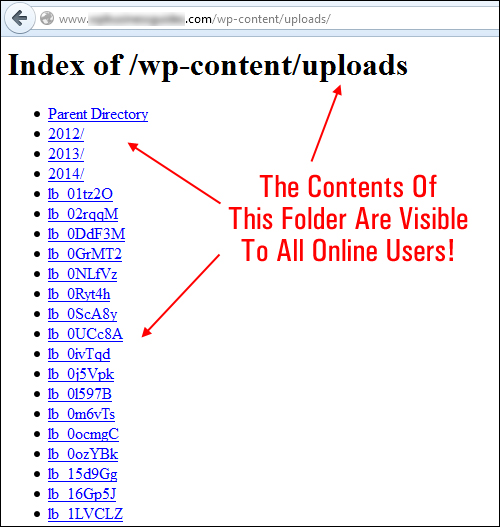
(WordPress uploads folder)
If any directories in your website have weaknesses or vulnerabilities that can be exploited by malicious users, this could become a serious threat to the security of your website.
Protecting your directories will prevent online users from viewing your ‘uploads’ folder and other important directories. This can be done using plugins, setting file permissions, uploading a blank index.php file (this is literally a file with nothing in it called “index.php”) to your uploads directory, and so on. Again, it’s best to use a professional if you are unsure about what to do.
Security Measure #10 – Use Security Plugins
There are several security plugins for WordPress available that specifically address many common security issues WordPress website owners face, such as preventing unauthorized users from gaining access to vital areas of your site, protecting your site from botnets, preventing unauthorized file uploads, etc.
Most WordPress plugins address some but not all areas of WordPress security. One security plugin that does a comprehensive job of scanning, fixing and preventing potential issues that could lead to hackers accessing your website files and damaging your site is SecureScanPro.
(SecureScanPro – total security software for WordPress)
SecureScanPro is easy to install and easy to use, and fixes most of the security issues that WordPress users need to address.
Another plugin you may want to look at using is BlogDefender.
Blog Defender Security Suite For WordPress Sites
This product is a suite of WordPress security video tutorials, plugins and tools, plus a WordPress security PDF/DOC file.
BlogDefender shows you where potential security weaknesses in your web site are …
 And lets you quickly fix these …
And lets you quickly fix these …
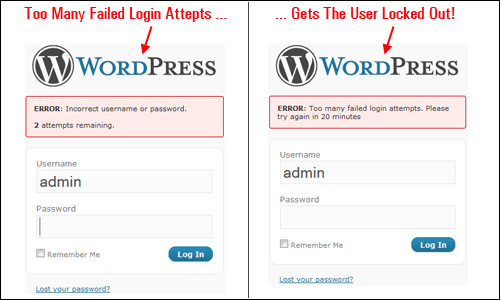
 If you don’t want to buy a security plugin like SecureScanPro or BlogDefender, then use various free WP plugins, such as Limit Login Attempts …
If you don’t want to buy a security plugin like SecureScanPro or BlogDefender, then use various free WP plugins, such as Limit Login Attempts …
WordPress is a secure web platform, but neglecting basic maintenance tasks like updating your WordPress installation, WordPress plugins and themes, tightening file and data security and taking other necessary precautions can expose your website to malicious by hackers and bots.
No matter what kind of business you run or plan to run online and how small you think your web presence is, website security is something you simply cannot afford to ignore.
As a final reminder of the importance of website security, below is the advice given by an expert on web security to all WordPress users following the mass brute force attacks on WordPress in April 2013 …
Owners of websites based on WordPress CMS must improve at least basic security settings and implement best practices such as the use of robust passwords and the accurate management of “admin” accounts.
Pierluigi Paganini, Chief Information Security Officer, Security Affairs
***
As you can see, website security is very important if you run a WordPress site. Hopefully, the information in this article has provided you with the initial guidelines and direction you need to keep your WordPress site protected from brute-force attacks. If you need any further help or assistance with WordPress security, please seek help from a WordPress security specialist, or search for a professional WordPress service provider in our WordPress Services Directory.
Also, do yourself a favor and subscribe to WPCompendium.org to receive notifications via email whenever we publish new tutorials on WordPress security and tutorials about WordPress security plugins.
***
"Wow! I never knew there's so much to learn about WordPress! I bought one of the WordPress for Dummies three years ago, such authors need to be on this course!" - Rich Law, Create A Blog Now
***