 This tutorial is part of our tutorial series on WordPress Security. In the previous section of this tutorial, looked at how to keep your computer operating system up-to-date. In this tutorial, we provide computer security tips and a downloadable “Basic Guide To Computer Security”.
This tutorial is part of our tutorial series on WordPress Security. In the previous section of this tutorial, looked at how to keep your computer operating system up-to-date. In this tutorial, we provide computer security tips and a downloadable “Basic Guide To Computer Security”.
Please also review our WordPress Security Guide For Beginners and our free WordPress Security Checklist.
***
Computer Security Tips
In addition to previous sections of this tutorial, the information below will help keep your computer devices safe and protected from hackers.
Password-protect your computer(s)
Your WordPress site can be compromised as simply and as easily as having someone access your computer and steal information containing your site’s login details.
The most basic way to keep your computer safe and protected is to require users to enter a password before being able to access your account.
To learn how to password-protect your computer, see the tutorial below:
Disable hidden filename extensions
By default, the Windows operating system is set to “hide file extensions for known file types”. Change this option so that file extensions do display in Windows. Some file extensions will, by default, continue to remain hidden, but you are more likely to see any unusual file extensions that should not be on your computer and you can then investigate further.
To enable/disable file extensions, click on the ‘Start’ button …
Choose ‘Control Panel’ …

In the ‘Control Panel’ screen, select ‘Appearance and Personalization’ …

Locate the ‘Folder Options’ section and click on ‘Show hidden files and folders’ …

In Folder Options > View tab, under ‘Advanced Settings’ find the ‘Hidden files and folders’ options and select ‘Show hidden files, folders and drives’, then click on ‘OK’ to enable this option …

Now, any files, folder and drives that were previously hidden will display in your computer browser screens …

Turn off your computer and disconnect from the network when not using the computer
A hacker cannot attack your computer when you are disconnected from the network or the computer is off.
Consider creating a system image, system repair disk and set system restore points at regular intervals
We’ve covered this earlier in the tutorial, but it’s worth repeating again. System images and repair disks are vital in case your computer is damaged or compromised by a malicious program. Obviously, you need to take these steps before you experience a hostile breach of your system.
Setting system restore points allows you to roll back your system to a previous point in time when everything was working fine (useful in case you install a program that messes up your computer).
To set a system restore point, click on Start > Computer …

Click on ‘System properties’ …

In the menu section, click on ‘System protection’ …

In the System Properties > System Protection tab, click the ‘Create’ button to create a system restore point …
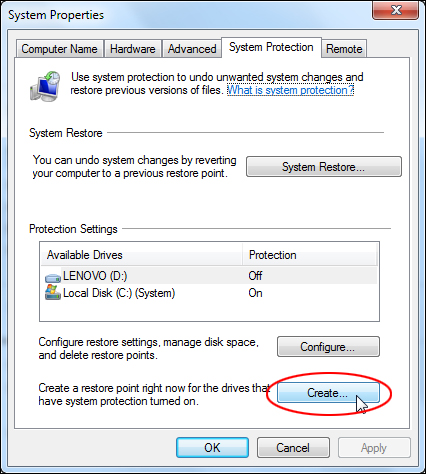
When the ‘System Restore’ window opens up, click on ‘Next’ …

Enter a description for your restore point and click the ‘Create’ button …

Your computer will begin to create a restore point …
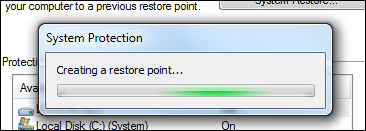
Once the restore point is create successfully, a notification message will display. Click the ‘Close’ button to continue …

To configure your System Restore settings, repeat the above steps to get to the ‘System protection’ tab, then click on the ‘Configure’ button …

Configure your ‘Restore Settings’ and adjust ‘Disk Space Usage’, then click on ‘OK’ to save your settings …

To restore your system back to a previous restore point, repeat the above process to view the ‘System Protection’ tab, and click on ‘System Restore’ …
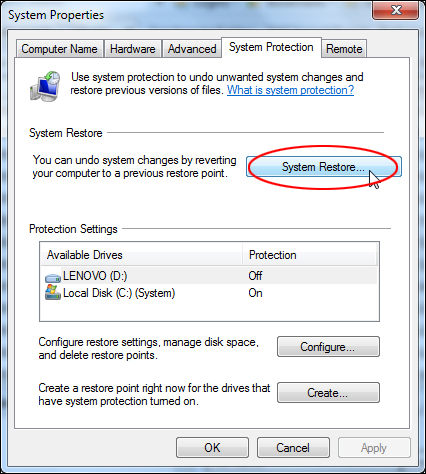
Select a restore point from the list displayed in your screen and click ‘Next’ to continue …

Confirm your restore point and click on ‘Finish’ to complete the process …

Your system will be restored to the state it was in previously.
Note: For best results, you should run System Restore from safe mode. If you receive an error while restoring, then restart your computer in safe mode and repeat the process and it should work fine. To get into Safe mode, reboot your computer and hold down the F8 key just before Windows starts up …

Lock your computer if you step away
If you are working around other people and decide to take a break from your computer, lock your computer. Even if you only step away for a few minutes, that’s enough time for someone to access your computer and destroy or steal your information. Locking your computer password-protects your session until you return and prevents anyone else from physically or remotely accessing your information …

Also, if you use laptops, try and keep public use and exposure to a minimum to reduce chances of device theft. Consider using a non-traditional laptop carrying case and an alarm or lock to add additional security.
If Selling Or Giving Your Computer Away …
If you plan to sell, donate, recycle or give your computer or laptop away, you should destroy all data and completely erase everything in your hard drive to ensure that no personal information can be obtained that could compromise your security.
We covered tools that can permanently destroy data on your computer in a previous tutorial (see Harden Your Computer Security).
If you want a total deletion of your hard drive (recommended if you are disposing of your computer), then you should consider using a program called Darik’s Boot and Nuke (DBAN) …

Darik’s Boot and Nuke (DBAN) is free erasure software designed for consumer use. DBAN is a self-contained boot disk that automatically deletes the contents of any hard disk that it can detect.
Using DBAN to delete everything on your hard drive can help prevent identity theft before recycling a computer. It is also a solution commonly used to remove viruses and spyware from Microsoft Windows installations. DBAN prevents all known techniques of hard disk forensic analysis.
![]()
Note: Once you run the program, there is no going back …

![]() DBAN makes users aware of some product limitations on its site, such as a disclaimer that it cannot guarantee that data will be removed, that it does not provide users with a proof of erasure, such as an audit-ready erasure report, and that it offers limited hardware support and no customer support.
DBAN makes users aware of some product limitations on its site, such as a disclaimer that it cannot guarantee that data will be removed, that it does not provide users with a proof of erasure, such as an audit-ready erasure report, and that it offers limited hardware support and no customer support.
To learn how to password-protect your computer, see the tutorial below:
Some final “common sense” computer security tips …
Use separate computers for business and leisure or personal activities
If possible, avoid using the same computer that you use for business or work, for personal online banking or shopping.
Company-assigned computers can be recalled for maintenance or upgrades, leaving your data exposed to others.
Also, if you have children and you let them use your computer to visit sites they like (e.g. games), you could potentially attract spyware and other risks into your device. Have your children keep a list of any sites they visit and don’t let them register on any web sites without your permission.
Keep your work and personal life on separate computers and you will limit the amount of cookies, spyware and monitoring that can take place, as well as reduce the incidence of identity theft.
Be careful when using public computers
Avoid banking or conducting personal business on public computers at libraries, hotels, and airports. Your online activity could be intercepted or recorded, or someone may be watching your activity and remembering passwords and other personal details.
Stay informed
Subscribe to sites like the National Cyber Alert System at www.us-cert.gov …
 Subscribing to trusted sites that deal with cyber security issues in a timely manner will help you stay informed and proactive when it comes to effectively protecting your home and business computers.
Subscribing to trusted sites that deal with cyber security issues in a timely manner will help you stay informed and proactive when it comes to effectively protecting your home and business computers.
Basic Guide To Computer Security
Download the free Basic Guide To Computer Security below …
[sociallocker id="6498"]Download the Basic Guide To Computer Security[/sociallocker]
Next Step:
Now that you know the basics of keeping your computer device secure, the next step is to learn how to protect your computer from malicious software and software-based security threats.
To learn more about keeping your computer protected from malicious software, see the tutorial below:
Computer Security Tutorials Review …
- Computer Security Guide For WordPress Users
- Creating A Computer BackUp System
- How To Add A Physical Layer Of Security Between Your Computer And The Internet
- How To Harden Your Computer Security
- How To Keep Your Computer Operating System Up-To-Date

(Source: Pixabay)
***
"These tutorials have so much information and are easy to understand. If you use WordPress or plan to in the future these will help you with everything you need to know." - Valisa (Mesa, Arizona)
***