![]() This tutorial is part of our tutorial series on WordPress Security. In this tutorial, we show you what to do if your WordPress site has been hacked or compromised.
This tutorial is part of our tutorial series on WordPress Security. In this tutorial, we show you what to do if your WordPress site has been hacked or compromised.
***
What To Do If Your WordPress Site Has Been Hacked
Note: If you are browsing this section and your site has not been compromised by an attack, then we recommend downloading and printing the accompanying “WP Hacked” report provided at the end of this tutorial as a safety precaution. This report contains a summary of the main instructions presented in this tutorial.
Backups are absolutely vital for website security and peace of mind!
As Benjamin Frankin once famously declared, “an ounce of prevention is worth a pound of cure.”
WordPress is a secure platform. If, however, your website has been compromised and you did not back up your WordPress site and data, then, unfortunately, there is very little you can do other than to reinstall WordPress and start again from scratch, or go through the painstakingly difficult process of trying to clean and recover your WordPress installation.
If you have set up the WordPress Maintenance System recommended in our WordPress Management Tutorials, then you should have all of your website’s data and files backed up, as well as a record of your email accounts, copies of any downloadable files you offer on your site (e.g. bonus reports for subscribers, etc.), additional content, etc. and this will make getting everything back up and running a lot easier, a lot faster and a lot less painful.
If your WordPress site has been hacked, or if you suspect that someone has compromised the security of your site, then follow the immediate steps provided below.
![]()
Note: Depending on your site, the urgency and nature of the attack, and the level of damage caused, you may not want to go through the process below yourself. If so, we recommend using the services of a professional website security expert!

WordPress Site Hacked – Immediate Action Steps
Here are the immediate action steps to take if you suspect that your WordPress site has been hacked:
Stay Calm
The first thing you need to do with any incident that involves security is to stay calm. This will help you think clearly as you go through the next steps, and prevent you from making any mistakes that can make your situation worse.
So … take a deep breath and calm yourself down before you do anything else …
Assess The Situation
The next step is to assess the situation. You want to be sure that your site has indeed been hacked before you take any drastic measures like shutting your entire business down online and/or deleting your entire site.
Sometimes things just act up. It could be that a plugin or application displays a weird WordPress error message, or your server temporarily goes down and your database stops working, or something just goes screwy.
For this reason, it’s important to stay calm. If you are not sure whether your site has indeed been hacked or not, then do the following:
1. (Optional): Go through our WordPress Troubleshooting Section information and make sure that you’re not just experiencing an error with your site that can be easily fixed.
To learn how to fix common WordPress errors, see the tutorial below:
2. Download and install the Exploit Scanner plugin if you can log into your site. This plugin can help detect any damage to your site so that it can be cleaned up.
Note: The WordPress Exploit Scanner plugin searches for malicious strings in your database but it doesn’t remove them. You have to remove all infections manually.
To download the Exploit Scanner plugin, visit the site below:
3. If you can’t log into your site or if you detect anything suspicious, notify your host immediately.
4. If you detect or suspect that any malicious code may have been injected into your website, then your machine may have been compromised. You will need to scan your hardware devices (e.g. laptop) for malware.
To learn more about securing your devices, see the tutorial below:
WordPress Site Hacked – Recovery Action Steps
Try To Regain Control
The next step is to try and get control of the situation if you can.
Depending on the nature of the attack, you may or may not be able to access your site.
In some cases, it may be possible to ‘clean’ up your WordPress installation and remove any malicious code your site has been infected with.
![]()
Tip: If you can’t login to your site, try simply deleting your .htaccess file. This usually solves many WordPress-related problems. If you have followed our WordPress maintenance tutorials you should a backup of your files, including a copy of your .htaccess file.
If you can access any of your hacked files or your WordPress database, then we recommend backing these up to a removable stick drive before deleting them from your hard drive or server.
This way, you can analyze your files for problems later (open source tools like OSSEC can analyze your logs and help you find where/how the attack happened), or send them off to a security expert for a ‘forensic’ investigation, or refer to them if you ever need to. Just remember to label the files as your ‘hacked site backup’ to avoid recreating the problem.
If you can access your site and you have determined that you site has been compromised, then do the following:
1. Change Passwords
Change passwords immediately for all of the following:
- Your WordPress Site Login Password – If you can access your WordPress site, see this tutorial: How To Reset Your WordPress Password. If you can’t access your WordPress site, try changing your password inside your MySQL file. Change passwords for all users, especially Administrators and Editors. This is especially important if you upload files to your site via FTP.
- Your WordPress Database Password – see this tutorial.
- Your FTP Password.
- Your Webhosting Account Password.
- Your Email Account Passwords.
- Any other passwords associated with your site.
![]()
Note: Changing some of the above passwords will most likely “break” your site (i.e. your website will stop being visible). Given the nature of the circumstances, however, this may not necessarily be a bad thing.
If your site has indeed been compromised and unwanted messages (e.g. spam) were being displayed on your site, then having your site no longer being visible will prevent your site visitors from seeing any offensive, disturbing or inappropriate content, protect the reputation of your site and help you avoid getting blocked by search engines, or even shut down by your host.
To learn more about Password Security, see the tutorial below:
2. Reinstall WordPress
In the most severe of circumstances, if your site has been badly compromised, or you have been locked out of your own site and can’t get back in, the safest thing to do is to simply delete everything and reinstall the latest version of WordPress.
![]()
![]()
![]()
If you have a recent back up of all of your site’s data and files, you can simply delete and recreate your hosting account, then perform a new WordPress installation and re-import all of your backed up data.
See the relevant tutorials in the training modules below for help reinstalling WordPress:
- WordPress Installation Tutorials: Installing WordPress Using cPanel
- WordPress Management Tutorials: Restoring WordPress Data
Note: Finding and removing malicious code from web files is a technically difficult area, and, therefore, outside the scope of these tutorials.
To learn more about cleaning up your WordPress installation and removing malicious code from a hacked website, read the articles below:
3. Update Plugins And Themes
After reinstalling WordPress, make sure that all of the plugins and themes you have reimported are up-to-date.
For help updating WordPress plugins and themes, see the tutorials below:
4. Update Your Security Keys
If a hacker steals your login details and they are logged into your site, they will remain logged in even if you change your password, because their browser cookies are still valid, and WordPress stores login session information using browser cookies.
To disable the cookies, you will need to create a new set of ‘security keys’ and replace your existing keys with the newly-created ones.
To learn how to create ‘Security Keys’ and how to add these to your WordPress site, see the tutorial below:
WordPress Site Hacked – Prevention Action Steps
Analyze What Happened
If you can find out how your website was hacked, you can help to prevent it from happening again (or at least try and prevent it from happening again in the same way!)
Here are some things you can do:
Google Your Site
Depending on how long it took to detect the hacking attack, your site may or may not have been picked up by search engines like Google as being potentially malicious to other users.
Google blacklists infected websites and warns visitors in its search engine results that clicking the link to visit the website could harm their computer …


It’s important, therefore, to check and see if your site has been blacklisted by Google.
To do this, simply Google your site address to see if a warning message like the one shown in the screenshot above (“This site may harm your computer”) is displayed.
If a warning is displayed, log into your Google Webmaster tools account …

After logging into your account and selecting your domain name, click on the ‘Security Issues’ section …
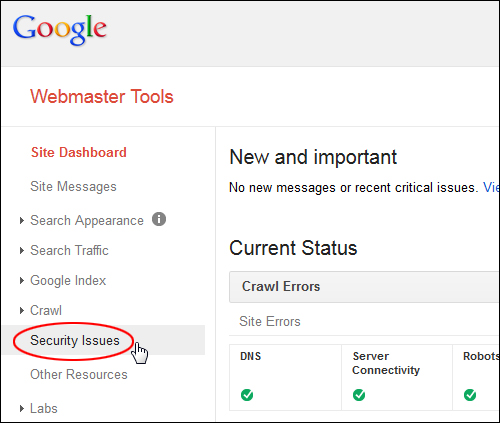

The ‘Security Issues’ screen displays all the security issues that Google has found and recorded for your site …


Even though you may have fixed these issues, Google will still blacklist your site until it is completely satisfied that all issues have been fixed.
To remove your site from Google’s blacklist, you will need to make sure that all of the security issues listed have been addressed and fixed before requesting Google to review your site.
To learn more about Google’s malware and hacked website notifications, visit the Google help page below:
For additional information on how to fix Google’s warning messages, visit the sites below:
Check Your .htaccess File For Hacks
Hackers can use your .htaccess file to redirect your site visitors to malicious sites.
If your WordPress installation is located in a subdirectory of your domain (e.g. yourdomain.com/blog), then look in the main folder’s .htaccess file as well. Hackers will try to hide their code at the bottom of the file, so scroll down.
Something else that a hacker may do is change the permissions of the .htaccess file to prevent you from editing the file. To make your file editable, change the file permission back to 644.
To learn how to set permissions for WordPress files and folders, see the tutorial below:
Upgrade Everything
Once you have a clean WordPress installation, make sure you upgrade your WordPress installation, plugins, and themes to their latest version. Older versions are more prone to hacks than newer versions.
Secure Your Site
After successfully recovering or reinstalling your site, make sure you secure it by implementing at least some of the recommended security measures in this training module (WordPress Security Tutorials).
To learn how to start making your WordPress site secure and protected from new attacks, see the tutorial below:
Change Your Passwords Again
If you only changed your passwords after discovering the hack, change them again after securing your new WordPress installation and making sure that your new site is clean.
Start Backing Up Regularly
After recovering from the nightmare and heartache of having your website hacked, it’s vitally essential that you learn how to start performing regular backups of your WordPress database and files.
This way, if your site ever gets hacked again, all you will need to do is restore your data and files from your last clean backup, and change your passwords and secret keys, and you’ll be back to normal again.
To learn how to create an effective WordPress maintenance and backup routine, see the relevant tutorials in the training module below:
Install Security Plugins
WordPress offers many great security plugins. Install one or more security plugins to protect your site from hackers and to prevent future attacks.
Check out the security plugins below:
- MalCare Security Service – One-Stop WordPress Security Solution
- WP Total Audit – Find And Fix Common WordPress Errors
- BulletProof Security Plugin For WordPress
Review Our WordPress Security Checklist
After completing all of the above steps, review our WordPress Security Checklist to ensure that your WordPress site is now fully protected and secure.
To view and download a printable copy of our free WordPress Security Checklist, go here:
![]()
![]()
The report below contains a summary of the action steps outlined in this tutorial. Download and print this document as a preventative measure in case your WordPress site gets hacked or ends up becoming compromised.
***
"These tutorials have so much information and are easy to understand. If you use WordPress or plan to in the future these will help you with everything you need to know." - Valisa (Mesa, Arizona)
***




